The Value of the Security Assessment

By: Jon Polly | Jul 25, 2022
The security industry has been labeled as ambulance chasers. It’s an honest label, as many security implementations only occur after a major incident, either to that user or others, and it is realized that the current risk mitigation strategies may not be adequate. Recent events such as the New York subway shooting and the Uvalde school shooting has prompted many organizations to make sudden reactionary security technology purchases. While this knee-jerk reaction to reduce the perceived attack has been seen repeatedly, it many times results in a revolving door of failure; failure where great technology was selected for the wrong application, or the right integration partner was overlooked for a myriad of reasons. The decisions inevitably result in increased risk, not less, and lost return on investment (ROI).
In the police department, the Range Master repeated the statement; “slow is smooth, smooth is fast.” The concept is to slow down, make smooth trigger pulls, take the time needed and make the shot count. Another way of saying that is “if a job is worth doing; do it right, once, and only once.” The same applies to partnering with customer organizations, especially those that needed answers yesterday. While the instinct is to help them as quickly as possible, the initial step must be to assess the current level of risk. Once the level of risk is truly known, the right process, technology solution, and/or partner(s) can be identified.
Physical security risk assessments can find problems before they begin and correct poor behaviors – such as propping doors open and ensuring locks and cameras work. They also provide the customer organization deliverable(s) that can be used to identify and prioritize risks, and metrics for evaluation. Security risk assessments are and should be a repeatable process after any major technology or methodology implementation. Physical security risk assessments have deliverables and should be charged to customer organizations, but risks should be evaluated with a technology agnostic mindset. Security risk assessments can be offered by independent third-party assessors such as a security consultant but can also be offered by an integration partner; the assessment should have a consultative approach and not appear biased. Herb Ubbens, President of Paratus Consultants Group articulates that, “The risk assessment should be looked at as the cornerstone of any program. When performed by persons with knowledge and experience in that field, the assessment can help you address operational issues and more importantly, provide insight into security and safety concerns as it relates to the Duty of Care that an employer or organization must provide a safe environment.”
Types of Assessments
There are three distinct types of security risk assessments that should be discussed with the customer organization, as each one of them can provide more information and direction. The below mentioned risk assessments are for physical security assessments but could be used for cybersecurity assessments or corporate risk management applications. The physical security risk assessment is not a gap analysis, though it can be part of the organization’s overall gap analysis process.
For each of these types of assessments there are checklists, templates, proprietary software, and homegrown spreadsheets to help identify the risk, vulnerability, or functionality. There is no one right deliverable. The goal is to provide the customer organization with the information they need to make an informed decision about the priority of risk, vulnerabilities, or technology to address.
The Risk Assessment
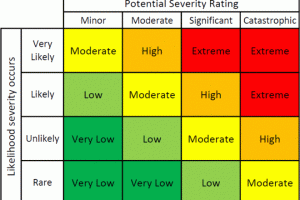
The risk assessment is a very probative assessment of not only the security risks, but many times includes operational risks, as well as safety and procedural reviews. The risk assessment typically involves a risk matrix that measures “Likelihood” and “Potential Severity.” For example, a severe risk, with no likelihood of ever happening would have less risk than a moderate risk, with a high likelihood of happening.
The risk assessment should evaluate both internal and external threats to the organization, and suggest ways to mitigate, transfer, avoid or accept the risk. Once risks are identified and mitigation strategies implemented what risk is left is considered “residual risk.” At that point, the organization can decide if the residual exposure or risk is tolerable to the organization or not. A full physical security risk assessment should include some background on the surrounding area of the organization, including direct threats to the organization as well as criminal activity in the surrounding area.
There is a two-part caution to risk assessments; 1) The assessor should hold an industry certification to understand the risks. An example would be the ASIS Physical Security Professional (PSP) equivalent or higher. 2) The Scope of Work should clearly state that only the physical security of the organization is going to be assessed, lest the assessment be hijacked in ways that could affect the assessor’s liability or errors and omissions (E&O) insurance policies.
The Vulnerability Assessment
A lesser version of the physical security assessment would be the vulnerability assessment. This assessment is still going to assess internal and external threats and should include homework on both direct threats to the organization as well as criminal activity in the surrounding area. Where the vulnerability assessment differs is that the assessor is looking for ways into the organization; failures in the physical building, technology, and people. A vulnerability assessment does not typically review polices or procedures. The vulnerability assessment has a strict scope of work, to assess all points of potential vulnerability for a threat; human, animal, or acts of God to gain entry or create damage to the organization.
Just like the risk assessment, the vulnerability assessment should be conducted by an assessor that holds an industry certification to understand the risks. An example would be the ASIS Physical Security Professional (PSP) equivalent or higher. The vulnerability can be assessed two ways; 1) As a penetration test, where the assessor assumes the role of a threat actor attempting to gain entry, or 2) as a reverse of the penetration test and assess the security from the inside out, in an attempt to identify weaknesses that could lead to vulnerabilities.
The Technology Audit
The reality is that many organizations may not necessarily need or want the risk or vulnerability assessment. While this can and probably should be argued slightly, there may be other influences preventing the full assessment.
The technology audit is simply a test of all existing technology to confirm functionality. Does the currently installed technology work in the manner that it was installed to do? A second question that then must be asked for reasons of the initial engagement, should it do more? While technology can be audited through any number of remote programs that are typically included with Service Level Agreements (SLA), a physical audit should be completed by the integration partner on at least a yearly basis, more if the customer organization has created Key Performance Indicators (KPIs) that can negatively affect the integration partner for failures. Herb Ubbens added that the adage, “what gets measured, gets managed,” is quite accurate and should be a part of every agreement.
Many times, the customer organization will request a technology audit when key employees have left or are leaving, to ensure the technology is accurately identified and located. The metrics for the audit are much simpler than those of the previous assessments, where the technology audit should include locating the technology on a drawing and identifying its functionality.
Unlike the previous assessments, the technology audit needs only be performed by a service technician or project manager knowledgeable of either the organization’s site, or in the types of technology the organization has deployed (if known).
Closing
Albert Einstein is credited with saying that the definition of insanity is “doing the same thing over and over and expecting different results.” Yet, this is exactly what many customer organizations experience when making sudden, reactionary purchases of technology. To reduce their attack surface, they inevitably create a larger risk to the entire technology ecosystem or even the organization, losing the ROI, not gaining. While the instinct for many is to purchase the widget or “shiny object,” it is a system of uncertain success. The first step when partnering with a customer organization must be to assess what they have, how it works together (or not), and define and measure the risk. Once this is completed the solution can be clearly identified. Is this methodology foolproof? No. Each implementation, interaction, process, and new risk can affect the variables. Assessments should be a repeated process after each implementation of technology or methodology, and on a set time basis to evaluate and measure the risk, vulnerability, or the technology.